Automated Pruning of OpenShift Artifacts; Builds, Deploys, Images
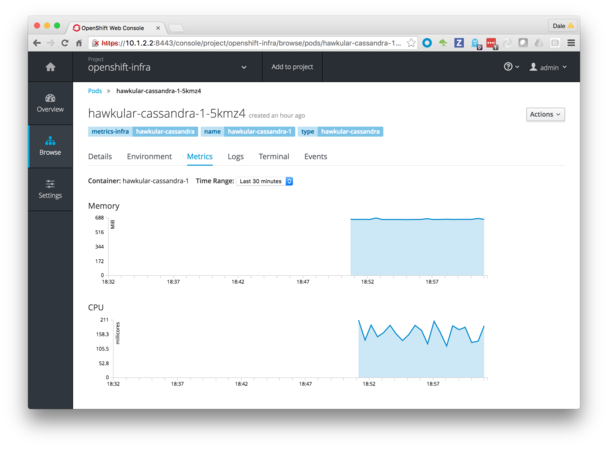
After running openshift for a while I discovered that letting builds pile up to around to around 1,200 led to what was essentially a deadlock in the scheduling of new builds. New builds were stuck in a New, waiting state indefinitely. This was fixed as of OCP 3.4.1, but it caused me to get more pro-active in the pruning of artifacts within OpenShift. I threw together a script and a playbook to deploy it.